#apache web-server
Explore tagged Tumblr posts
Text
How to Automatically Restart Failed Services in Linux Using Monit
When running production servers, ensuring your critical services stay up and running is essential. Service failures can happen for various reasons — memory issues, unexpected crashes, or resource limitations. Fortunately, Linux offers reliable solutions to automatically monitor and restart failed services without requiring constant manual intervention. Server reliability is crucial for…
#Apache#automation#email alerts#high availability#Linux#linux services#monit#Monit Service Manager#monit web gui#monit web login#MySQL#nginx#server administration#server management#service monitoring#system reliability#web server
0 notes
Text
Cara Tepat Memasang SSL/TLS Pakai Apache & Nginx di Localhost Linux
Halom Pembaca! HTTPS merupakan standar keamanan via web yang paling banyak diimplementasikan saat ini. Tidak dapat dipungkiri, pengembangan situs web tahap staging di Localhost terkadang membutuhkan enkripsi SSL/TLS. Namun, Certificate Authority ternama seperti Let’s Encrypt, Comodo, dan Digicert tidak mau memberikan sertifikat untuk situs Localhost (beralamat IP 127.0.0.0 s.d. 127.255.255.255),…
0 notes
Text
Un día como hoy (1 de diciembre) en la computacion

El 1 de diciembre de 1995 se libera la primera versión del software para servidores web Apache HTTP, basado en el NCSA HTTPd, y que ha jugado un rol primordial en el crecimiento inicial y exponencial del WWW. Hoy, ocupa el segundo lugar, atrás por dos puntos a Nginx, como de lo más usados para servir sitios web #retrocomputingmx #apache #http #webserver
0 notes
Text
Apache Web Server? What It Is and How It Works 2023
Apache web server, a well liked open source, cross platform web server The Apache Software Foundation regularly
0 notes
Text
Want to know what is Apache server? Learn how Apache works to power your web experience & Explore Apache Server's functionality and operation.
#what is an apache server#what is apache server#what is apache server and how it works#what is apache web server
0 notes
Text
Unleashing the Power of Apache: Expert Web Server Design in Washington
In the digital age, having a powerful and reliable web server is essential for businesses to thrive online. Apache, one of the most widely used web server software, offers a robust and flexible platform to host websites and applications. If you are looking to harness the full potential of Apache web server design Washington then we are here to help with our team of expert professionals.
At 2NetSolutions, we specialize in creating tailored web server solutions that leverage the power of Apache. Our team of skilled professionals understands the intricacies of Apache and its various modules, allowing us to design and implement a web server environment that meets your unique requirements.
From initial planning and configuration to ongoing maintenance and optimization, we guide you through every step of the process. Our goal is to create a web server setup that is efficient, secure, and scalable, ensuring that your website or application performs at its best under any circumstances.
With our expert web server design in Washington, you can expect a seamless user experience, improved website speed, and enhanced security. We take into account factors such as traffic volume, server load, and future growth projections to design a robust architecture that can handle your current and future needs.
Additionally, our team provides comprehensive support and monitoring services to ensure that your web server continues to operate at peak performance. We proactively identify and address any issues, minimizing downtime and maximizing uptime.
Don’t settle for a subpar web server setup that hampers your online presence. Unleash the power of Apache with our expert web server design services in Washington.

Efficient Installation and Configuration Solutions in Washington: Streamline Your Business Operations
In today’s fast-paced business landscape, having a well-functioning and optimized technology infrastructure is crucial for the success of any organization. Efficient installation and configuration of your IT systems can make a significant difference in streamlining your business operations and boosting productivity. If you are based in Washington, we offer top-notch installation and configuration solutions that are tailored to meet your specific needs.
At 2NetSolutions, we understand the importance of a seamless technology setup. Our team of experienced professionals is well-versed in the latest installation and configuration Washington techniques to ensure that your systems are up and running smoothly. Whether it’s setting up networks, servers, software applications, or security protocols, we have the expertise to handle it all.
By choosing our installation and configuration services, you can save valuable time and resources while enjoying a hassle-free experience. Our meticulous approach ensures that every aspect of your IT infrastructure is optimized for maximum efficiency and reliability. With our solutions in place, you can focus on what you do best — growing your business.
Don’t let technology hurdles slow you down. Contact us today for efficient installation and configuration solutions in Washington and take your business operations to the next level.
0 notes
Text









Hotmail service was founded by Sabeer Bhatia and Jack Smith, and was one of the first webmail services on the Internet along with Four11's RocketMail (later Yahoo! Mail). It was commercially launched on July 4, 1996, symbolizing "freedom" from ISP-based email and the ability to access a user's inbox from anywhere in the world. The name "Hotmail" was chosen out of many possibilities ending in "-mail" as it included the letters HTML, the markup language used to create web pages (to emphasize this, the original type casing was "HoTMaiL"). The limit for free storage was 2 MB. Hotmail was initially backed by venture capital firm Draper Fisher Jurvetson. By December 1997, it reported more than 8.5 million subscribers. Hotmail initially ran under Solaris for mail services and Apache on FreeBSD for web services, before being partly converted to Microsoft products, using Windows Services for UNIX in the migration path.
Hotmail was sold to Microsoft in December 1997 for a reported $400 million (~$705 million in 2023), and it joined the MSN group of services. The sale had been preceded by a major incident in 1997 where all email was lost for 25% of mailboxes. Hotmail quickly gained in popularity as it was localized for different markets around the globe, and became the world's largest webmail service with more than 30 million active members reported by February 1999.
Hotmail originally ran on a mixture of FreeBSD and Solaris operating systems. A project was started to move Hotmail to Windows 2000. In June 2001, Microsoft claimed this had been completed; a few days later they retracted the statement and admitted that the DNS functions of the Hotmail system were still reliant on FreeBSD. In 2002 Hotmail still ran its infrastructure on UNIX servers, with only the front-end converted to Windows 2000. Later development saw the service tied with Microsoft's web authentication scheme, Microsoft Passport (now Microsoft account), and integration with Microsoft's instant messaging and social networking programs, MSN Messenger and MSN Spaces (later Windows Live Messenger and Windows Live Spaces, respectively).
#hotmail#msn#90s www#90s web#90s internet#vintage internet#vintage computing#outlook#microsoft#Bandcamp
27 notes
·
View notes
Text
I’m sorry but I’m still losing my fucking MIND over elons incomprehensible Linux own the libs tweet like
Like it’s incredibly obvious he heard about a traceroute, and then googled “how to delete file in Linux” and then didn’t even read the results
Like… woke_mind_virus isn’t a fully qualified domain name, meaning it relies on a custom DNS resolution specific to his machine, or if utilizing a vpn, that specific vpn’s custom host file. Or that the American government would have a host entry for a woke mind virus, which if you’ve ever had to use a government website, is laughable. Also DNS is global for the most part, but honestly we can move on at this point.
So sure, we’ll say that the government has forced all public internet in America to resolve woke_mind_virus. Where does it resolve to? YOUR OWN COMPUTER, you silly billy! Obviously! This is *almost* comprehensible. Sure, we are all infected with the woke mind virus, why not. It must be destroyed within ourselves. Yeah man, whatever. Why not? So how do we destroy it?
Duh! Just delete it! How do we do that in our L337 uber hax0r terminal on our fresh kali live usb (because partitions are scary)? We’ll save that for last.
Because while deleting one file could make a website inoperable, it does not remove every trace of it! It first needs a configuration file in the web server, usually Apache or nginx. This is at LEAST one file, but cmon, if you’re gonna psychologically program the masses and keep it out of public view, you gotta encrypt that shit! So naturally, an SSL is in order! That’s easily 1-3 more files. woke_mind_virus can get a pass on not being fully qualified in this specific case because certs can theoretically be self signed and trusted on local networks, but he wouldn’t be able to tell you that. If you stood up a little one page html site on a web server on your own computer, and navigated to it on port 443 (https://) you would get an SSL error, even though it’s on your own machine. I feel like I’ve beaten this into the ground enough, but just understand it’s stupid.
What’s important to note here is that these BARE MINIMUM files are what routes the request from your machine to the destination site, even if it’s your own computer. If you delete the contents of the site (also called the docroot), the site still exists, and can receive and route requests to and from it, it’s just empty. You’ll probably get a 404 because there’s no actual content to serve. This woke mind princess is in another castle.
It’s also imprudent to delete these configuration files first, because that’s how you determine where the site content actually is! These files dictate what directory (folder for you windows losers) is called upon to actually serve you the content you see displayed when you open a webpage. So you need this information if you don’t want to destroy the entire file system and only want to remove the woke_mind_virus site. Cmon Elon, this is baby shit.
So of course, the strat with the most Efficiency and preserving the rest of the system (which seems to be the point of the tweet) is to find the docroot, delete the docroot, and then delete the web server config files. So how do we delete them?
And here we have it: rm -rf
The syntax is as follows:
rm -rf </path/to/file>
Even if you don’t know shit about Linux, you can probably see the problem here. It’s just so blatantly incorrect, it’s almost as if he’s never done it before.
For those that want to see a real world example, here is me creating a file called woke_mind_virus in my home directory and then trying to delete it the Elon Way:
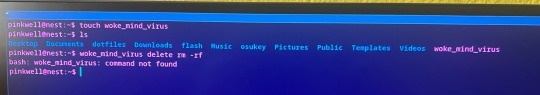
3 notes
·
View notes
Text
Secure Your Laravel App: Fix Insufficient Transport Layer Security (TLS)
Introduction
Transport Layer Security (TLS) is vital for ensuring secure communication between clients and servers over the Internet. Insufficient TLS configurations can leave your Laravel web applications exposed to various cyber threats, like Man-in-the-Middle (MitM) attacks. In this blog post, we’ll explain the risks associated with insufficient TLS security in Laravel and provide a detailed guide on how to configure your Laravel application for optimal security.

Additionally, we’ll show you how to check and resolve potential TLS issues using our free Website Security Scanner tool.
What is Insufficient Transport Layer Security?
Insufficient Transport Layer Security occurs when a website fails to use strong encryption protocols like TLS 1.2 or higher, or when it doesn't properly configure SSL certificates. This exposes web applications to data interception, tampering, and attacks. A properly configured TLS ensures that all data transmitted between the server and client is encrypted and secure.
Common Issues in Laravel with Insufficient TLS Security
Some common causes of insufficient TLS in Laravel include:
Outdated SSL Certificates: Using deprecated SSL/TLS protocols (like SSL 3.0 or TLS 1.0) that are no longer considered secure.
Improper SSL/TLS Configuration: Misconfiguration of the web server or Laravel app that doesn’t force HTTPS or downgrade protection.
Weak Cipher Suites: Servers using weak ciphers, making it easier for attackers to break the encryption.
Lack of HTTP Strict Transport Security (HSTS): Without HSTS, an attacker can force the browser to use an insecure HTTP connection instead of HTTPS.
How to Fix Insufficient TLS in Laravel
Upgrade Your Laravel App’s TLS Protocol To enforce TLS 1.2 or higher, you'll need to configure your server to support these protocols. Here’s how you can configure your server to prioritize stronger encryption:
In Apache: Modify the ssl.conf file:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
In Nginx: Edit your nginx.conf file:
ssl_protocols TLSv1.2 TLSv1.3;
These configurations will ensure that your server uses only secure versions of TLS.
2. Force HTTPS in Laravel Laravel provides an easy way to force HTTPS by modifying the .env file and the config/app.php file:
In .env file:
APP_URL=https://yourdomain.com
In config/app.php file:
'url' => env('APP_URL', 'https://yourdomain.com'),
This will ensure that all requests are redirected to HTTPS, preventing insecure HTTP access.
3. Enable HTTP Strict Transport Security (HSTS) HTTP Strict Transport Security is a web security policy mechanism that helps to protect websites against Man-in-the-Middle (MitM) attacks by forcing clients to communicate over HTTPS. Here's how to add HSTS headers to your Laravel app:
In Apache: Add the following line to your ssl.conf or .htaccess file:
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
In Nginx: Add the following line to your nginx.conf file:
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;
4. Use Strong Cipher Suites Weak cipher suites allow attackers to break the encryption. You can configure your server to use strong ciphers:
In Apache:
SSLCipherSuite HIGH:!aNULL:!MD5:!3DES
In Nginx:
ssl_ciphers 'ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256';
5. Use a Valid SSL/TLS Certificate Ensure that your website uses a valid SSL/TLS certificate from a trusted Certificate Authority (CA). You can get a free SSL certificate from Let's Encrypt.
How to Check TLS Configuration with Our Free Tool
Before and after implementing the changes, it’s essential to check the security status of your website. You can use our free Website Security Checker Tool to evaluate your website’s TLS configuration.
Go to https://free.pentesttesting.com.
Enter your website URL to start the scan.
Review the vulnerability assessment report for TLS issues.
Screenshot of the Free Tool
Here’s a screenshot of the free Website Security Checker tool in action:

Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of a Vulnerability Assessment Report
After running the scan to check website vulnerability, you’ll receive a detailed report highlighting any security vulnerabilities, including issues related to TLS. Here’s an example of the vulnerability assessment report:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
Ensuring sufficient Transport Layer Security in your Laravel app is crucial to protecting sensitive data and preventing attacks. By following the steps outlined in this blog, you can fix any TLS issues and enhance the security of your web application.
Don’t forget to check your website using our free Website Security Checker tool to identify any existing TLS vulnerabilities and other security flaws.
Need help? Contact us at Pentest Testing Corp for professional vulnerability assessments and penetration testing services to secure your website further.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#tls
4 notes
·
View notes
Text
What Is Linux Web Hosting? A Beginner's Guide
In the ever-evolving digital landscape, the choice of web hosting can significantly impact your online presence. One of the most popular options available is Linux web hosting. But what exactly does it entail, and why is it so widely preferred? This beginner’s guide aims to demystify Linux web hosting, its features, benefits, and how it stands against other hosting types.
Introduction to Web Hosting
Web hosting is a fundamental service that enables individuals and organisations to make their websites accessible on the internet. When you create a website, it consists of numerous files, such as HTML, images, and databases, which need to be stored on a server. A web host provides the server space and connectivity required for these files to be accessed by users online.
There are several types of web hosting, each designed to cater to different needs and budgets. Shared hosting is a cost-effective option where multiple websites share the same server resources. Virtual Private Server (VPS) hosting offers a middle ground, providing dedicated portions of a server for greater performance and control. Dedicated hosting provides an entire server exclusively for one website, ensuring maximum performance but at a higher cost. Cloud hosting uses multiple servers to balance the load and maximise uptime, offering a scalable solution for growing websites.
Web hosting services also include various features to enhance the performance and security of your website. These can range from basic offerings like email accounts and website builders to more advanced features like SSL certificates, automated backups, and DDoS protection. The choice of web hosting can significantly influence your website’s speed, security, and reliability, making it crucial to choose a solution that aligns with your specific requirements.
Understanding the different types of web hosting and the features they offer can help you make an informed decision that suits your needs. Whether you are running a personal blog, a small business website, or a large e-commerce platform, selecting the right web hosting service is a critical step in establishing a successful online presence.
What Is Linux Web Hosting?
Linux web hosting is a type of web hosting service that utilises the Linux operating system to manage and serve websites. Renowned for its open-source nature, Linux provides a stable and secure platform that supports a wide array of programming languages and databases, making it a favoured choice amongst developers and businesses. This hosting environment typically includes support for popular technologies such as Apache web servers, MySQL databases, and PHP scripting, which are integral to modern website development.
One of the distinguishing features of Linux web hosting is its cost-effectiveness. As an open-source system, Linux eliminates the need for costly licensing fees associated with proprietary software, thereby reducing overall hosting expenses. This makes it an attractive option for individuals and organisations operating on a budget.
Moreover, Linux is celebrated for its robust performance and high stability. Websites hosted on Linux servers experience less downtime and faster loading times, which are critical factors for maintaining user engagement and search engine rankings. The operating system’s extensive community of developers continuously works on updates and improvements, ensuring that Linux remains a cutting-edge choice for web hosting.
Linux web hosting also offers considerable flexibility and customisation options. Users have the freedom to configure their hosting environment to meet specific needs, whether they are running simple static websites or complex dynamic applications. This versatility extends to compatibility with various content management systems (CMS) like WordPress, Joomla, and Drupal, which often perform optimally on Linux servers.
In summary, Linux web hosting provides a reliable, secure, and cost-effective solution that caters to a diverse range of web hosting requirements. Its compatibility with essential web technologies and its inherent flexibility make it a preferred choice for many web developers and site owners.
Key Benefits of Linux Web Hosting
Linux web hosting offers several compelling advantages that contribute to its widespread adoption. One of its primary benefits is cost-effectiveness. The open-source nature of Linux eliminates the need for expensive licensing fees, allowing users to allocate their resources more efficiently. This makes it an ideal choice for individuals and organisations with budget constraints. Additionally, Linux is celebrated for its high stability and robust performance. Websites hosted on Linux servers often experience minimal downtime and faster loading speeds, which are essential for maintaining user engagement and achieving favourable search engine rankings.
Another significant benefit is the extensive community support that comes with Linux. The active community of developers and enthusiasts continuously works on updates, patches, and security enhancements, ensuring that Linux remains a secure and reliable platform for web hosting. This ongoing development also means that any issues or vulnerabilities are promptly addressed, offering peace of mind for website owners.
Flexibility is another key advantage of Linux web hosting. The operating system supports a wide range of programming languages, including PHP, Python, and Ruby, making it suitable for various types of web applications. Additionally, Linux servers are highly customisable, allowing users to configure their environment to meet specific needs, whether they are running simple static sites or complex dynamic applications.
Moreover, Linux web hosting is highly compatible with popular content management systems (CMS) like WordPress, Joomla, and Drupal. This compatibility ensures that users can easily deploy and manage their websites using these platforms, benefiting from their extensive plugin and theme ecosystems.
Lastly, Linux's superior security features are worth noting. The operating system is inherently secure and offers various built-in security measures. When combined with best practices such as regular updates and strong passwords, Linux web hosting provides a highly secure environment for any website.
Understanding Linux Distributions in Web Hosting
Linux comes in a variety of distributions, each tailored to meet specific needs and preferences. Among the most popular for web hosting are Ubuntu, CentOS, and Debian. Ubuntu is celebrated for its ease of use and extensive community support, making it a great choice for those new to Linux. CentOS, a favourite in enterprise environments, offers impressive stability and long-term support, which ensures a dependable hosting experience. Debian stands out with its robust package management system and commitment to open-source principles, providing a reliable and secure foundation.
Each distribution brings its own strengths to the table. For example, Ubuntu’s frequent updates ensure access to the latest features and security patches, while CentOS’s extended support cycles make it a solid choice for those requiring a stable, long-term hosting environment. Debian’s extensive repository of packages and minimalistic approach offers flexibility and customisation, catering to the needs of experienced users.
Selecting the right Linux distribution largely depends on your specific requirements and technical expertise. If you prioritise user-friendliness and a wealth of resources for troubleshooting, Ubuntu might be the ideal pick. On the other hand, if you need a rock-solid, stable platform for an enterprise-level application, CentOS could be more appropriate. For those seeking maximum control and a commitment to open-source principles, Debian is a compelling option.
Ultimately, understanding the nuances of these distributions will enable you to choose a Linux environment that aligns with your web hosting needs, ensuring optimal performance and reliability.
Linux Hosting vs Windows Hosting: A Comparative Analysis
When evaluating Linux hosting against Windows hosting, several critical factors come into play. Cost is a significant differentiator; Linux hosting is generally more affordable due to its open-source nature, which eliminates the need for expensive licensing fees. In contrast, Windows hosting often incurs additional costs related to proprietary software licenses.
Compatibility is another important aspect to consider. Linux hosting is renowned for its compatibility with a broad array of open-source software and applications, including popular content management systems like WordPress, Joomla, and Magento. These platforms typically perform better on Linux servers due to optimised server configurations. On the other hand, Windows hosting is the go-to option for websites that rely on Microsoft-specific technologies such as ASP.NET, MSSQL, and other .NET frameworks.
Performance and stability are also crucial elements in this comparison. Linux hosting often provides superior uptime and faster loading speeds due to the lightweight nature of the Linux operating system. The robust performance of Linux servers is further enhanced by the active community that continuously works on optimisations and security patches. Windows hosting, while also reliable, can sometimes be more resource-intensive, potentially affecting performance.
Customisation and control levels differ significantly between the two. Linux offers greater flexibility and customisation options, allowing users to tweak server settings and configurations extensively. This level of control is particularly beneficial for developers who need a tailored hosting environment. Conversely, Windows hosting is typically easier to manage for those familiar with the Windows operating system but may offer less flexibility in terms of customisation.
Security measures also vary between Linux and Windows hosting. Linux is often praised for its strong security features, which are bolstered by a large community dedicated to promptly addressing vulnerabilities. While Windows hosting is secure, it may require more frequent updates and maintenance to ensure the same level of protection.
Common Use Cases for Linux Web Hosting
Linux web hosting is versatile and caters to a broad range of applications, making it a popular choice across various sectors. One of the most common use cases is hosting blogs and personal websites, particularly those built on platforms like WordPress. The open-source nature of Linux and its compatibility with PHP make it an ideal environment for WordPress, which powers a significant portion of the web.
E-commerce websites also benefit greatly from Linux web hosting. Solutions like Magento, PrestaShop, and OpenCart often perform better on Linux servers due to their need for a robust, secure, and scalable hosting environment. The flexibility to configure server settings allows online store owners to optimise performance and ensure a smooth shopping experience for their customers.
Content Management Systems (CMS) such as Joomla and Drupal are another prime use case. These systems require reliable and flexible hosting solutions to manage complex websites with large amounts of content. Linux's support for various databases and scripting languages ensures seamless integration and optimal performance for CMS-based sites.
Developers frequently turn to Linux web hosting for custom web applications. The operating system supports a variety of programming languages, including Python, Ruby, and Perl, making it suitable for a wide array of development projects. Its command-line interface and extensive package repositories allow developers to install and manage software efficiently.
Additionally, Linux web hosting is commonly used for educational and non-profit websites. The low cost and high reliability make it a practical choice for schools, universities, and charitable organisations that need a dependable online presence without breaking the bank.
Setting Up a Linux Web Hosting Environment
Setting up a Linux web hosting environment can be straightforward with the right approach. Begin by selecting a reputable hosting provider that offers Linux-based plans. After signing up, you'll typically be granted access to a control panel, such as cPanel or Plesk, which simplifies the management of your hosting environment. Through the control panel, you can manage files, databases, email accounts, and more.
Next, if you're using a content management system (CMS) like WordPress, Joomla, or Drupal, you can often find one-click installation options within the control panel. This feature makes it easy to get your website up and running quickly. Additionally, ensure that you configure your domain name to point to your new hosting server, which usually involves updating your domain's DNS settings.
For those who prefer more control or are comfortable using the command line, you can manually set up your web server using SSH access. This method allows you to install and configure web server software like Apache or Nginx, as well as databases such as MySQL or PostgreSQL.
Regardless of the setup method you choose, it's crucial to secure your server from the outset. This includes setting up a firewall, enabling SSH key authentication for secure access, and regularly updating all software to protect against vulnerabilities. Regularly monitoring your server's performance and security logs can help you stay ahead of potential issues, ensuring a stable and secure hosting environment for your website.
Security Best Practices for Linux Web Hosting
Securing your Linux web hosting environment is paramount to safeguarding your website against potential threats. Begin by ensuring your server software and all installed applications are up to date. Regular updates often include patches for security vulnerabilities, making this a critical step. Utilise strong, unique passwords for all user accounts, and consider employing SSH key authentication for added security when accessing your server remotely.
Setting up a firewall is another essential measure. Tools like iptables or firewalld can help you configure firewall rules to control incoming and outgoing traffic, thereby reducing the risk of unauthorised access. Implementing intrusion detection systems (IDS), such as Fail2Ban, can provide an additional layer of security by monitoring and blocking suspicious activities.
Consider deploying an SSL certificate to encrypt data transmitted between your server and users' browsers. This not only enhances security but also boosts user trust and can improve your search engine rankings. Additionally, limit the use of root privileges; create separate user accounts with the necessary permissions to minimise potential damage in the event of a breach.
Regularly backup your data to mitigate the impact of data loss due to hardware failure, cyber-attacks, or human error. Automated backup solutions can simplify this process, ensuring your data is consistently protected. Monitoring your server's logs can also be invaluable for identifying unusual activity early. Tools like Logwatch or the ELK Stack can assist in log management and analysis, enabling you to take swift action if anomalies are detected.
Common Challenges and How to Overcome Them
Setting up and maintaining a Linux web hosting environment can present various challenges, especially for those new to the platform. One frequent issue is navigating the command line, which can be daunting for beginners. Engaging with online tutorials, forums, and communities like Stack Overflow can be invaluable for learning the basics and troubleshooting problems. Another common challenge is software incompatibility. Ensuring your web applications are compatible with the Linux distribution you choose is crucial; consulting documentation and support resources can help mitigate these issues.
Security configuration can also be a complex task. Implementing best practices such as setting up firewalls, regular updates, and using strong authentication methods requires a good understanding of Linux security principles. Managed hosting services can offer a solution here by handling these technical aspects for you, allowing you to focus on your website content.
Resource management is another area where users might struggle. Monitoring server performance and managing resources effectively ensures your website runs smoothly. Utilising monitoring tools and performance optimisation techniques can help you stay ahead of potential issues. Lastly, when it comes to server backups, regular, automated solutions are essential to prevent data loss and minimise downtime. Being proactive in addressing these challenges will ensure a more seamless and secure Linux web hosting experience.
Popular Control Panels for Linux Web Hosting
Control panels are invaluable for simplifying the management of your Linux web hosting environment. Among the most popular are cPanel, Plesk, and Webmin. cPanel is renowned for its intuitive interface and extensive feature set, making it a favourite among users who need a straightforward yet powerful management tool. Plesk offers robust functionality and supports both Linux and Windows servers, providing versatility for those who manage multiple server environments. Webmin stands out as a free, open-source option that allows comprehensive server management through a web interface, catering to those who prefer a customisable and cost-effective solution. Each control panel brings unique strengths, helping to streamline tasks such as file management, database administration, and security configurations.
Choosing the Right Linux Web Hosting Provider
Choosing the right Linux web hosting provider involves several key considerations. Firstly, evaluate the quality of customer support offered. Responsive and knowledgeable support can be invaluable, especially when troubleshooting technical issues or during the initial setup phase. Check if the provider offers 24/7 support and multiple contact methods such as live chat, email, and phone.
Another crucial factor is the security measures in place. Opt for providers that offer robust security features, including regular backups, SSL certificates, firewalls, and DDoS protection. These features help safeguard your website against potential threats and ensure data integrity.
Reliability and uptime guarantees are also vital. Aim for providers that offer at least a 99.9% uptime guarantee, as frequent downtimes can significantly affect your website’s accessibility and user experience. Additionally, look into the provider’s data centre infrastructure and redundancy measures, which can impact overall performance and reliability.
Scalability is another important aspect to consider. As your website grows, you’ll need the flexibility to upgrade your hosting plan seamlessly. Check if the provider offers scalable solutions, such as easy transitions to VPS or dedicated hosting, without causing disruptions to your site.
Lastly, consider the hosting plans and pricing structures available. While cost-effectiveness is a significant benefit of Linux web hosting, ensure the plans align with your specific needs. Compare the features, storage, bandwidth, and other resources included in different plans to find the best value for your money.
Reading customer reviews and seeking recommendations can also provide insights into the provider’s reputation and service quality. By carefully evaluating these factors, you can choose a Linux web hosting provider that meets your requirements and supports your online endeavours effectively.
Conclusion and Final Thoughts
Linux web hosting stands out as an optimal choice for both beginners and seasoned web developers. Its open-source nature provides an affordable, highly customisable, and secure environment, suitable for a diverse range of websites, from personal blogs to large e-commerce platforms. The extensive community support ensures ongoing improvements and prompt resolution of issues, contributing to its reliability and performance. Choosing the right hosting provider is crucial; look for robust security measures, excellent customer support, and scalability to accommodate your website's growth. By leveraging the strengths of Linux web hosting, you can build a resilient and efficient online presence that meets your specific needs and goals.
4 notes
·
View notes
Text

SYSTEM ADMIN INTERVIEW QUESTIONS 24-25
Table of Content
Introduction
File Permissions
User and Group Management:
Cron Jobs
System Performance Monitoring
Package Management (Red Hat)
Conclusion
Introduction
The IT field is vast, and Linux is an important player, especially in cloud computing. This blog is written under the guidance of industry experts to help all tech and non-tech background individuals secure interviews for roles in the IT domain related to Red Hat Linux.
File Permissions
Briefly explain how Linux file permissions work, and how you would change the permissions of a file using chmod. In Linux, each file and directory has three types of permissions: read (r), write (w), and execute (x) for three categories of users: owner, group, and others. Example: You will use chmod 744 filename, where the digits represent the permission in octal (7 = rwx, 4 = r–, etc.) to give full permission to the owner and read-only permission to groups and others.
What is the purpose of the umask command? How is it helpful to control default file permissions?umask sets the default permissions for newly created files and directories by subtracting from the full permissions (777 for directories and 666 for files). Example: If you set the umask to 022, new files will have permissions of 644 (rw-r–r–), and directories will have 755 (rwxr-xr-x).
User and Group Management:
Name the command that adds a new user in Linux and the command responsible for adding a user to a group. The Linux useradd command creates a new user, while the usermod command adds a user to a specific group. Example: Create a user called Jenny by sudo useradd jenny and add him to the developer’s group by sudo usermod—aG developers jenny, where the—aG option adds users to more groups without removing them from other groups.
How do you view the groups that a user belongs to in Linux?
The group command in Linux helps to identify the group a user belongs to and is followed by the username. Example: To check user John’s group: groups john
Cron Jobs
What do you mean by cron jobs, and how is it scheduled to run a script every day at 2 AM?
A cron job is defined in a crontab file. Cron is a Linux utility to schedule tasks to run automatically at specified times. Example: To schedule a script ( /home/user/backup.sh ) to run daily at 2 AM: 0 2 * * * /home/user/backup.sh Where 0 means the minimum hour is 2, every day, every month, every day of the week.
How would you prevent cron job emails from being sent every time the job runs?
By default, cron sends an email with the output of the job. You can prevent this by redirecting the output to /dev/null. Example: To run a script daily at 2 AM and discard its output: 0 2 * * * /home/user/backup.sh > /dev/null 2>&1
System Performance Monitoring
How can you monitor system performance in Linux? Name some tools with their uses.
Some of the tools to monitor the performance are: Top: Live view of system processes and usage of resource htop: More user-friendly when compared to the top with an interactive interface. vmstat: Displays information about processes, memory, paging, block IO, and CPU usage. iostat: Showcases Central Processing Unit (CPU) and I/O statistics for devices and partitions. Example: You can use the top command ( top ) to identify processes consuming too much CPU or memory.
In Linux, how would you check the usage of disk space?
The df command checks disk space usage, and Du is responsible for checking the size of the directory/file. Example: To check overall disk space usage: df -h The -h option depicts the size in a human-readable format like GB, MB, etc.
Package Management (Red Hat)
How do you install, update, or remove packages in Red Hat-based Linux distributions by yum command?
In Red Hat and CentOS systems, the yum package manager is used to install, update, or remove software. Install a package: sudo yum install httpd This installs the Apache web server. Update a package: sudo yum update httpd Remove a package:sudo yum remove httpd
By which command will you check the installation of a package on a Red Hat system?
The yum list installed command is required to check whether the package is installed. Example: To check if httpd (Apache) is installed: yum list installed httpd
Conclusion
The questions are designed by our experienced corporate faculty which will help you to prepare well for various positions that require Linux such as System Admin.
Contact for Course Details – 8447712333
2 notes
·
View notes
Text
How to Automatically Restart Failed Services in Linux Using systemd
When running production servers, ensuring your critical services stay up and running is essential. Service failures can happen for various reasons — memory issues, unexpected crashes, or resource limitations. Fortunately, modern Linux distributions include systemd, which offers built-in functionality to automatically restart failed services without requiring constant manual intervention. Server…
#Apache#automation#high availability#Linux#linux services#MySQL#nginx#server administration#server management#service monitoring#system reliability#systemd#web server
0 notes
Text
NVIDIA AI Workflows Detect False Credit Card Transactions

A Novel AI Workflow from NVIDIA Identifies False Credit Card Transactions.
The process, which is powered by the NVIDIA AI platform on AWS, may reduce risk and save money for financial services companies.
By 2026, global credit card transaction fraud is predicted to cause $43 billion in damages.
Using rapid data processing and sophisticated algorithms, a new fraud detection NVIDIA AI workflows on Amazon Web Services (AWS) will assist fight this growing pandemic by enhancing AI’s capacity to identify and stop credit card transaction fraud.
In contrast to conventional techniques, the process, which was introduced this week at the Money20/20 fintech conference, helps financial institutions spot minute trends and irregularities in transaction data by analyzing user behavior. This increases accuracy and lowers false positives.
Users may use the NVIDIA AI Enterprise software platform and NVIDIA GPU instances to expedite the transition of their fraud detection operations from conventional computation to accelerated compute.
Companies that use complete machine learning tools and methods may see an estimated 40% increase in the accuracy of fraud detection, which will help them find and stop criminals more quickly and lessen damage.
As a result, top financial institutions like Capital One and American Express have started using AI to develop exclusive solutions that improve client safety and reduce fraud.
With the help of NVIDIA AI, the new NVIDIA workflow speeds up data processing, model training, and inference while showcasing how these elements can be combined into a single, user-friendly software package.
The procedure, which is now geared for credit card transaction fraud, might be modified for use cases including money laundering, account takeover, and new account fraud.
Enhanced Processing for Fraud Identification
It is more crucial than ever for businesses in all sectors, including financial services, to use computational capacity that is economical and energy-efficient as AI models grow in complexity, size, and variety.
Conventional data science pipelines don’t have the compute acceleration needed to process the enormous amounts of data needed to combat fraud in the face of the industry’s continually increasing losses. Payment organizations may be able to save money and time on data processing by using NVIDIA RAPIDS Accelerator for Apache Spark.
Financial institutions are using NVIDIA’s AI and accelerated computing solutions to effectively handle massive datasets and provide real-time AI performance with intricate AI models.
The industry standard for detecting fraud has long been the use of gradient-boosted decision trees, a kind of machine learning technique that uses libraries like XGBoost.
Utilizing the NVIDIA RAPIDS suite of AI libraries, the new NVIDIA AI workflows for fraud detection improves XGBoost by adding graph neural network (GNN) embeddings as extra features to assist lower false positives.
In order to generate and train a model that can be coordinated with the NVIDIA Triton Inference Server and the NVIDIA Morpheus Runtime Core library for real-time inferencing, the GNN embeddings are fed into XGBoost.
All incoming data is safely inspected and categorized by the NVIDIA Morpheus framework, which also flags potentially suspicious behavior and tags it with patterns. The NVIDIA Triton Inference Server optimizes throughput, latency, and utilization while making it easier to infer all kinds of AI model deployments in production.
NVIDIA AI Enterprise provides Morpheus, RAPIDS, and Triton Inference Server.
Leading Financial Services Companies Use AI
AI is assisting in the fight against the growing trend of online or mobile fraud losses, which are being reported by several major financial institutions in North America.
American Express started using artificial intelligence (AI) to combat fraud in 2010. The company uses fraud detection algorithms to track all client transactions worldwide in real time, producing fraud determinations in a matter of milliseconds. American Express improved model accuracy by using a variety of sophisticated algorithms, one of which used the NVIDIA AI platform, therefore strengthening the organization’s capacity to combat fraud.
Large language models and generative AI are used by the European digital bank Bunq to assist in the detection of fraud and money laundering. With NVIDIA accelerated processing, its AI-powered transaction-monitoring system was able to train models at over 100 times quicker rates.
In March, BNY said that it was the first big bank to implement an NVIDIA DGX SuperPOD with DGX H100 systems. This would aid in the development of solutions that enable use cases such as fraud detection.
In order to improve their financial services apps and help protect their clients’ funds, identities, and digital accounts, systems integrators, software suppliers, and cloud service providers may now include the new NVIDIA AI workflows for fraud detection. NVIDIA Technical Blog post on enhancing fraud detection with GNNs and investigate the NVIDIA AI workflows for fraud detection.
Read more on Govindhtech.com
#NVIDIAAI#AWS#FraudDetection#AI#GenerativeAI#LLM#AImodels#News#Technews#Technology#Technologytrends#govindhtech#Technologynews
2 notes
·
View notes
Text
Progress so far of mobile server (dev log)
So I was successful in turning my old phone into apache web server. The phone had some hardware issue that it always clicked on the screen randomly so I had to maneuverer my way installing Linux and apache into the phone. I had to set up proxies as well to connect to it with the open internet. So far it is working well. Sometimes I have to reroute the connections since it is running over mobile data? I am thinking of getting a dynamic DNS. But I have never tried dynamic DNS before so I am not ready to explore that yet. Plus, I don't know if I would get a static IP from it or a straight away domain name? I mean both are okay, but both have pros and cons of the usage.
Like if I get a static IP , I can run virtual hosts in apache and run multiple websites pointing A record of the domain to the same website.
And lets say if I get a subdomain from the dynamic DNS, I can point CNAME record of the domain to subdomain? But will virtual hosts work with it? I don't know. I suppose it should but it could not work also. Hmm.. lets see, I think I have done this before, apache virtual hosts works with CNAME.
But there is another issue that one of the website runs behind a SOCKS5 proxy, How will I accommodate that? The issue is that, since its Ubuntu running over VM over lineage OS in phone, I can't get low number ports such 80 or 443 so I have to somehow use Dynamic DNS and SOCKS5 proxy to redirect traffic at higher port number.
I mean, I still have oracle VPS running so I may not need virtual hosts in mobile server. So maybe I will venture this when I need it.
I am just wondering whether I should run Docker to run my game server then redirect the traffic with apache virtual hosts, reverse proxy with SOCKS5 proxy? I don't even know if it work. Theoretically it should work.
14 notes
·
View notes
Text
Exploring the Realm of cPanel Hosting in Australia: A Comprehensive Guide
In the vast digital landscape of Australia, where businesses thrive and online presence is paramount, finding the right hosting solution is akin to selecting a foundation for a skyscraper. In this digital age, where websites serve as the face of enterprises, the choice of hosting can significantly impact performance, user experience, and ultimately, the success of ventures. Among the plethora of options, cPanel hosting stands out as a popular choice for its user-friendly interface, robust features, and reliability. But what exactly is cPanel hosting, and why is it gaining traction among businesses in Australia?

Understanding cPanel Hosting
What is cPanel hosting?
cPanel hosting is a type of web hosting that utilizes the cPanel control panel, a web-based interface that simplifies website and server management tasks. It provides users with a graphical interface and automation tools, allowing them to effortlessly manage various aspects of their website, such as file management, email accounts, domain settings, databases, and more.
How does cPanel Hosting Work?
At its core, cPanel hosting operates on a Linux-based server environment, leveraging technologies like Apache, MySQL, and PHP (LAMP stack). The cPanel interface acts as a centralized hub, enabling users to perform administrative tasks through a user-friendly dashboard, accessible via any web browser.
Benefits of cPanel Hosting
User-Friendly Interface
One of the primary advantages of cPanel hosting is its intuitive interface, designed to accommodate users of all skill levels. With its graphical layout and straightforward navigation, even those with minimal technical expertise can manage their websites efficiently.
Comprehensive Feature Set
From creating email accounts to installing applications like WordPress and Magento, cPanel offers a wide array of features designed to streamline website management. Users can easily configure domains, set up security measures, and monitor website performance, and much more, all from within the cPanel dashboard.
Reliability and Stability
cPanel hosting is renowned for its stability and reliability, thanks to its robust architecture and frequent updates. With features like automated backups, server monitoring, and security enhancements, users can rest assured that their websites are in safe hands.
Scalability and Flexibility
Whether you're running a small blog or managing a large e-commerce platform, cPanel hosting can scale to meet your needs. With options for upgrading resources and adding additional features as your website grows, cPanel offers the flexibility required to adapt to evolving business requirements.
Choosing the Right cPanel Hosting Provider
Factors to Consider
When selecting a cPanel hosting provider in Australia, several factors should be taken into account to ensure optimal performance and reliability:
Server Location: Choose a provider with servers located in Australia to minimize latency and ensure fast loading times for local visitors.
Performance: Look for providers that offer high-performance hardware, SSD storage, and ample resources to support your website's needs.
Uptime Guarantee: Opt for providers with a proven track record of uptime, ideally offering a minimum uptime guarantee of 99.9%.
Customer Support: Evaluate the level of customer support offered, ensuring prompt assistance in case of technical issues or inquiries.
Conclusion
In conclusion, cPanel hosting serves as a cornerstone for businesses seeking reliable and user-friendly cpanel hosting Australia. With its intuitive interface, comprehensive feature set, and robust architecture, cPanel empowers users to manage their websites with ease, allowing them to focus on their core business objectives.
2 notes
·
View notes
Text
Unveiling Java's Multifaceted Utility: A Deep Dive into Its Applications
In software development, Java stands out as a versatile and ubiquitous programming language with many applications across diverse industries. From empowering enterprise-grade solutions to driving innovation in mobile app development and big data analytics, Java's flexibility and robustness have solidified its status as a cornerstone of modern technology.

Let's embark on a journey to explore the multifaceted utility of Java and its impact across various domains.
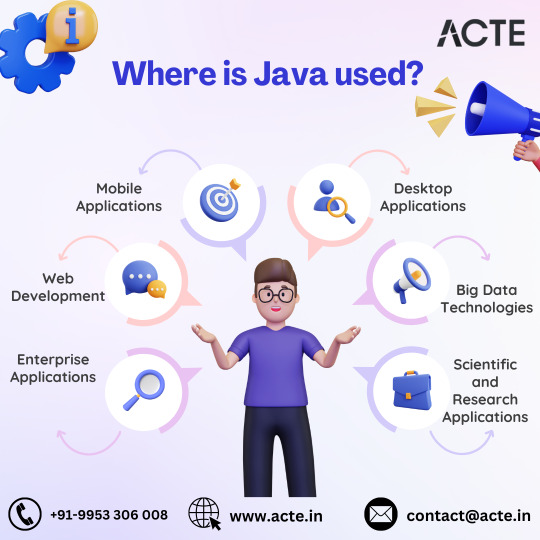
Powering Enterprise Solutions
Java is the backbone for developing robust and scalable enterprise applications, facilitating critical operations such as CRM, ERP, and HRM systems. Its resilience and platform independence make it a preferred choice for organizations seeking to build mission-critical applications capable of seamlessly handling extensive data and transactions.
Shaping the Web Development Landscape
Java is pivotal in web development, enabling dynamic and interactive web applications. With frameworks like Spring and Hibernate, developers can streamline the development process and build feature-rich, scalable web solutions. Java's compatibility with diverse web servers and databases further enhances its appeal in web development.
Driving Innovation in Mobile App Development
As the foundation for Android app development, Java remains a dominant force in the mobile app ecosystem. Supported by Android Studio, developers leverage Java's capabilities to craft high-performance and user-friendly mobile applications for a global audience, contributing to the ever-evolving landscape of mobile technology.
Enabling Robust Desktop Solutions
Java's cross-platform compatibility and extensive library support make it an ideal choice for developing desktop applications. With frameworks like Java Swing and JavaFX, developers can create intuitive graphical user interfaces (GUIs) for desktop software, ranging from simple utilities to complex enterprise-grade solutions.
Revolutionizing Big Data Analytics
In big data analytics, Java is a cornerstone for various frameworks and tools to process and analyze massive datasets. Platforms like Apache Hadoop, Apache Spark, and Apache Flink leverage Java's capabilities to unlock valuable insights from vast amounts of data, empowering organizations to make data-driven decisions.
Fostering Innovation in Scientific Research
Java's versatility extends to scientific computing and research, where it is utilized to develop simulations, modeling tools, and data analysis software. Its performance and extensive library support make it an invaluable asset in bioinformatics, physics, and engineering, driving innovation and advancements in scientific research.
Empowering Embedded Systems
With its lightweight runtime environment, Java Virtual Machine (JVM), Java finds applications in embedded systems development. From IoT devices to industrial automation systems, Java's flexibility and reliability make it a preferred choice for building embedded solutions that require seamless performance across diverse hardware platforms.
In summary, Java's multifaceted utility and robustness make it an indispensable tool in the arsenal of modern software developers. Whether powering enterprise solutions, driving innovation in mobile app development, or revolutionizing big data analytics, Java continues to shape the technological landscape and drive advancements across various industries. As a versatile and enduring programming language, Java remains at the forefront of innovation, paving the way for a future powered by cutting-edge software solutions.
2 notes
·
View notes